Protecting sensitive data and applications in today’s interconnected world is paramount for businesses of all sizes.
A virtual private server (VPS) offers a robust platform for hosting websites, applications, and services, but its security hinges on careful configuration and a strong defense.
Implementing a comprehensive firewall is crucial to safeguard your VPS from malicious attacks, unauthorized access, and data breaches.
Secure VPS hosting with a firewall forms a critical security layer, ensuring the confidentiality, integrity, and availability of your digital assets.
The benefits of a robust firewall extend beyond basic security; they enhance the reliability and resilience of your entire online presence.
A well-designed firewall acts as a gatekeeper, scrutinizing all network traffic and filtering out unwanted access attempts.
This carefully calibrated approach to secure VPS hosting is essential for maintaining a healthy digital ecosystem, preventing operational disruptions, and safeguarding the reputation of your organization.
This article delves into the intricacies of secure VPS hosting with firewall implementation, exploring its importance, the different types of firewalls, and the configurations needed for maximum protection.
By understanding and implementing these strategies, businesses can confidently navigate the complexities of online security and ensure the protection of their valuable digital assets and data.
The underlying foundation of this security architecture, secure VPS hosting with a firewall, demands careful consideration to avoid vulnerabilities and threats in today’s rapidly evolving digital landscape.
A secure firewall on your VPS hosting is no longer a luxury, but a necessity for modern businesses to ensure data protection, maintain uptime, and avoid potential financial repercussions.
The Essential Role of Firewalls in Secure VPS Hosting
A robust firewall is a critical component of any secure VPS hosting solution, acting as the first line of defense against external threats.
This crucial security measure ensures the confidentiality, integrity, and availability of data hosted on the VPS, a vital aspect in modern digital environments.
Implementing a firewall with a secure VPS hosting setup establishes a secure perimeter, isolating the server environment from potential vulnerabilities inherent in shared hosting.
The firewall meticulously filters incoming and outgoing network traffic, examining each packet for compliance with predefined security rules.
By restricting unauthorized access attempts, the firewall actively prevents malicious actors from infiltrating the VPS environment and exploiting potential security weaknesses.
Its role goes beyond simply blocking unwanted connections; it also actively monitors network activity for unusual patterns or anomalies, providing early warnings of potential attacks.
This proactive approach to network security is crucial in the face of increasingly sophisticated cyber threats and helps minimize the risk of data breaches or service disruptions.
A firewall’s ability to scrutinize incoming traffic is paramount for preventing unauthorized access from hackers and malware.
Proper firewall configuration is directly linked to the overall security posture of the VPS, impacting its resilience to attacks such as denial-of-service (DoS) attacks or intrusion attempts.
Regular updates and proactive maintenance of the firewall are essential for maintaining its effectiveness and adaptability to emerging threats.
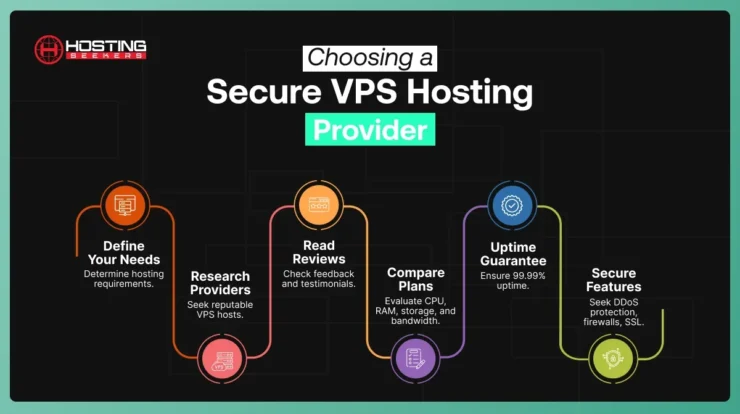
Choosing a secure VPS hosting provider that prioritizes firewall implementation and ongoing maintenance is vital for long-term security and a smooth operational experience.
The integration of a firewall into the VPS hosting environment is an essential element of a comprehensive security strategy, significantly improving the protection of critical data and applications.
A properly configured firewall in a secure VPS hosting environment significantly reduces the risk of security breaches and enhances the overall reliability of the hosting infrastructure.
Customizable Firewall Rules for Enhanced Security
A vital aspect of secure VPS hosting involves implementing a firewall with highly customizable rules. This allows for a granular control over network traffic, tailoring security measures to specific application needs.
This granular control extends beyond basic blocking and enables the identification and mitigation of particular attack vectors, providing a more proactive security posture.
Sophisticated firewalls can be configured with rulesets that permit specific traffic types and deny others, further enhancing the security of the VPS environment.
These rulesets allow for the blocking of malicious IP addresses or port ranges, proactively obstructing potential threats before they can access the VPS.
By implementing specific rules relating to network protocols, such as SSH or HTTP, administrators can restrict access to applications and services only to authorized entities.
Implementing custom firewall rules empowers administrators to control access to critical VPS resources and services, a crucial step for robust security management. This customization is particularly valuable in the context of secure vps hosting, providing targeted defense against specific threats.
Further, these custom rules can be updated in response to emerging vulnerabilities, ensuring the continuous adaptation of the security framework to evolving threats and maintaining a layered security approach, a necessity for modern VPS environments. This capability is a significant benefit of secure vps hosting.
This dynamic approach to firewall management allows administrators to tailor the security posture based on specific business requirements, optimizing the security configuration for diverse needs. This adaptability is a defining characteristic of a robust secure VPS hosting solution.
The advanced capabilities of customizable firewall rules provide a critical component for secure vps hosting, effectively mitigating the risk of unwanted network access and safeguarding sensitive data from cyberattacks.
By allowing precise control of network traffic, customizable firewall rules deliver a significantly enhanced security layer for the VPS environment, addressing a critical concern of modern digital businesses. Implementing robust, adaptable, and granular firewall rules offers an essential layer of protection for virtual private servers.
In summary, the ability to customize firewall rules offers a powerful tool for secure VPS hosting, providing flexibility, enhanced security, and adaptation to evolving threats, resulting in an adaptable and secure platform for the digital business.
Choosing the Right Firewall Rules for Secure VPS Hosting
Implementing a robust firewall is paramount for secure VPS hosting, but the true strength lies in strategically configuring firewall rules to precisely control network traffic.
A poorly configured firewall can leave your VPS vulnerable to attacks and compromise your data security, emphasizing the critical importance of careful firewall rule definition.
This involves establishing clear, granular controls over incoming and outgoing connections, dictating which ports and protocols are permitted or blocked.
A well-defined firewall strategy is not a one-size-fits-all solution; it necessitates understanding the specific applications and services running on the VPS and adjusting firewall rules accordingly.
The core principle of secure VPS hosting with firewall is to allow only the necessary network traffic, blocking everything else.
For instance, if your VPS hosts a web server, you would configure the firewall to permit HTTP and HTTPS traffic on port 80 and 443, respectively, while blocking all other incoming connections on those ports to prevent unauthorized access.
Similarly, if you use SSH to manage your VPS, you must allow SSH traffic (port 22) through the firewall.
The correct configuration of firewall rules also protects against malicious actors who might exploit vulnerabilities in applications or operating systems by blocking their corresponding ports.
A critical aspect is understanding your VPS’s services and applications, allowing only essential protocols and ports to facilitate their operation.
This meticulous approach to firewall rule creation is crucial for preventing unauthorized access, which in turn protects your data and resources.
Detailed logging of firewall events is essential to monitor suspicious activities and identify potential security breaches promptly.
Further, regularly updating the firewall ruleset with new applications and security patches is vital for sustained protection.
Using a firewall with a strong set of preconfigured rules based on your server’s services and known security best practices can provide a baseline for a secure VPS hosting environment. This tailored strategy for secure VPS hosting with firewall demonstrates a proactive approach to security, minimizing the potential attack surface and bolstering your system’s resilience against evolving threats.
The level of sophistication in firewall rules, dependent on the complexity of your setup, should reflect the specific vulnerabilities and security needs of your Virtual Private Server (VPS).
A comprehensive understanding of the services running on your VPS is essential for configuring effective firewall rules, ensuring your security posture is tailored to the specific demands of your hosting environment. This detailed approach to firewall management is a cornerstone of secure VPS hosting.
Security Auditing and Compliance
Regular security audits are crucial for maintaining the integrity and trustworthiness of a virtual private server (VPS) hosting environment, especially when utilizing a robust firewall.
These audits assess the effectiveness of security measures, including the firewall configurations, and identify potential vulnerabilities that malicious actors might exploit.
Comprehensive audits should cover the firewall rules themselves, checking for any gaps or unnecessary openings that could compromise the VPS.
This process involves scrutinizing the firewall’s configuration to ensure it aligns with current security best practices and company policies, minimizing potential attack vectors.
Furthermore, audits should encompass the operating system and application configurations, searching for outdated software or misconfigurations that could be exploited.
Maintaining compliance with industry standards, such as PCI DSS or HIPAA, is often a critical aspect of a secure VPS hosting setup, which is dependent on the correct firewall implementation and configuration.
Regular penetration testing, often part of the security auditing process, can simulate real-world attacks to expose vulnerabilities and evaluate the effectiveness of the firewall’s defenses.
These tests provide valuable insights into the strengths and weaknesses of the secure vps hosting setup and provide a baseline for continuous improvement.
Through meticulous security audits, organizations can proactively identify and remediate vulnerabilities, ensuring the highest levels of security for their data and applications hosted on the VPS.
By integrating robust security audits into the regular maintenance schedule for their secure vps hosting, organizations can demonstrate a commitment to protecting sensitive information and build trust with clients and stakeholders.
Finally, maintaining a detailed audit log of all security-related activities provides a valuable record for troubleshooting and incident response, should a security breach occur.
In today’s interconnected digital landscape, safeguarding sensitive data and maintaining operational resilience is paramount for businesses of all sizes.
The robust security offered by secure VPS hosting with a firewall provides an indispensable layer of protection, shielding your applications and data from unauthorized access and malicious attacks.
This article highlighted the critical importance of strong firewalls in conjunction with dedicated virtual server infrastructure, emphasizing how they prevent vulnerabilities and safeguard your valuable assets, ensuring uninterrupted business operations.
Choosing secure VPS hosting with a firewall is not just about mitigating risks; it’s about proactively building a reliable and trustworthy online presence. The sophisticated configuration options and customizable rulesets allow for tailored protection against a wide range of threats, from simple intrusion attempts to complex cyberattacks.
Implementing secure VPS hosting with firewall functionalities empowers businesses to maintain a high level of data security and minimizes the potential for costly downtime and reputational damage. The detailed discussion of configuration methods and best practices provided throughout this article underscores the crucial role of secure VPS hosting with firewall in creating a robust and resilient digital environment, protecting your investments and enabling sustainable growth.
Ultimately, adopting secure VPS hosting with firewall isn’t just a security measure; it’s a strategic investment that safeguards your digital assets, promotes business continuity, and ensures your online operations remain uninterrupted and reliable in the face of ever-evolving cyber threats.