Protecting your online presence requires a robust defense system, and secure hosting with a firewall plays a crucial role in safeguarding your data and applications.
Today’s interconnected digital world exposes businesses and individuals to a constant barrage of cyber threats, ranging from malicious software to sophisticated hacking attempts.
A comprehensive approach to online security necessitates a secure hosting environment that employs sophisticated firewalls to deter unauthorized access and maintain the integrity of your valuable data.
This strategy, employing secure hosting with firewall, creates a fortified perimeter around your online assets, significantly mitigating the risks of data breaches and system compromise.
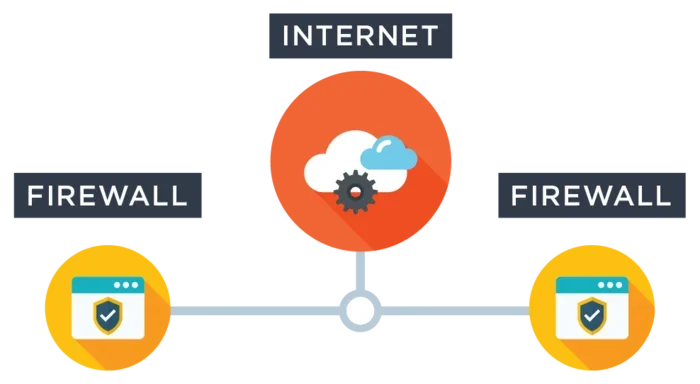
A firewall acts as a gatekeeper, meticulously scrutinizing incoming and outgoing network traffic, filtering out suspicious activity and only allowing authorized connections to access your hosted resources.
This proactive approach to security ensures that only legitimate users and applications can interact with your systems, thereby preserving the confidentiality, integrity, and availability of your critical information.
Businesses heavily reliant on online platforms, like e-commerce stores, web applications, and cloud services, particularly benefit from a well-configured secure hosting solution with a robust firewall, greatly minimizing vulnerabilities and maintaining user trust.
Beyond protecting against unwanted intrusions, a dependable secure hosting environment equipped with a firewall fosters a secure and reliable online experience for your clients and customers, ultimately bolstering your reputation and operational efficiency.
Implementing secure hosting with firewall safeguards your sensitive data from breaches, ensuring that only authorized personnel can access your servers and applications.
By understanding the importance of these security measures, you can create a resilient system that safeguards your online assets and enhances your organization’s overall security posture.
The Critical Role of Firewalls in Secure Hosting
A robust firewall is an essential component of any secure hosting solution, acting as a critical first line of defense against external threats.
Implementing a firewall on your hosting server establishes a secure perimeter around your online assets, effectively shielding them from malicious actors attempting unauthorized access.
This proactive security measure significantly reduces the risk of data breaches and system compromise, which can have devastating consequences for businesses and individuals alike.
Secure hosting, with a firewall as its integral part, creates a controlled environment, allowing only authorized traffic to reach your systems.
A well-configured firewall meticulously examines incoming and outgoing network traffic, identifying and blocking suspicious activity that could jeopardize the security of your data and applications.
This meticulous screening process filters out malicious software, denial-of-service attacks, and other harmful network activities that compromise the integrity of your hosting environment and the confidentiality of your data.
Different firewall types offer varying levels of protection, each tailored to specific security needs.
For instance, a stateful firewall maintains a record of established connections, enabling it to filter traffic based on connection state and history, providing a more sophisticated defense against attacks.
A firewall’s effectiveness in a secure hosting environment depends on its proper configuration and ongoing maintenance.
Regular updates, security patches, and careful monitoring are paramount to maintaining its effectiveness against evolving threats.
Choosing a hosting provider that prioritizes security and offers a high-performance firewall is a strategic decision for safeguarding your digital assets.
A dedicated team of security professionals monitoring and maintaining the firewall can further enhance its protective capabilities.
This proactive approach ensures your hosting environment remains shielded from a wide range of cyber threats and maintains the integrity of your valuable data.
In essence, a secure hosting solution with a robust firewall is not just a best practice but a necessary measure in today’s interconnected digital landscape.
The Critical Role of Firewalls in Secure Hosting
A robust firewall is an essential component of any secure hosting solution, acting as a critical first line of defense against external threats.
Implementing a firewall on your hosting server establishes a secure perimeter around your online assets, effectively shielding them from malicious actors attempting unauthorized access.
This proactive security measure significantly reduces the risk of data breaches and system compromise, which can have devastating consequences for businesses and individuals alike.
Secure hosting, with a firewall as its integral part, creates a controlled environment, allowing only authorized traffic to reach your systems.
A well-configured firewall meticulously examines incoming and outgoing network traffic, identifying and blocking suspicious activity that could jeopardize the security.
Firewall configurations are customized to meet the specific security needs of each hosting environment, ensuring that the appropriate level of protection is applied to safeguard valuable data.
This customization is crucial for effectively countering diverse security threats, ranging from simple denial-of-service attacks to intricate, targeted exploits.
The firewall’s ability to filter network traffic is a fundamental aspect of its functionality, ensuring only legitimate requests are processed by the hosting platform.
This stringent filtering process acts as a substantial barrier, hindering potential attackers from gaining unauthorized access to sensitive data or system resources.
Furthermore, firewalls protect against various threats, such as malicious software and intrusions, safeguarding the integrity of hosted data and applications.
A properly implemented firewall often includes intrusion detection and prevention systems (IDS/IPS) to proactively identify and mitigate emerging threats.
These security measures strengthen the overall security posture of the hosting environment, minimizing vulnerabilities and protecting against a wide array of potential attacks.
Modern firewalls leverage advanced technologies to recognize and block sophisticated attacks, such as zero-day exploits.
This capability is essential for maintaining a secure hosting environment in the face of ever-evolving cyber threats.
Implementing advanced security protocols through a firewall ensures the longevity of secure hosting by preventing unauthorized access, data breaches, and system compromise.
In addition to its primary function of blocking unauthorized access, firewalls can also log and monitor network activity.
These logs are invaluable for troubleshooting network issues and identifying potential security breaches.
Through a comprehensive logging mechanism, firewalls provide a record of network events for subsequent analysis and security enhancement.
The comprehensive nature of firewall-based security solutions makes them an indispensable part of a modern security strategy.
Ultimately, a robust firewall is a key component for providing secure hosting that protects sensitive information, assets, and reputation.
Secure Access Management and User Authentication
Robust secure hosting necessitates meticulous control over who can access the hosted resources, a crucial aspect often overlooked in the pursuit of simply establishing a firewall.
Implementing secure access management and user authentication mechanisms is vital for preventing unauthorized access and data breaches, which are paramount in the modern digital landscape.
This critical aspect of secure hosting involves not only restricting access through the firewall but also meticulously verifying the identity of users attempting to interact with the hosted applications or data. This security measure is foundational in preventing unauthorized users from infiltrating the system and gaining access to sensitive information.
Secure access management encompasses various techniques, including strong password policies, multi-factor authentication (MFA), and role-based access control (RBAC). Each technique plays a significant role in fortifying the overall security posture of the hosting environment.
Strong password policies mandate complex passwords, regular password changes, and prohibit the reuse of passwords across multiple accounts. These policies effectively deter unauthorized access attempts by making it more difficult for attackers to guess or crack passwords.
Multi-factor authentication adds another layer of security by requiring users to provide more than one form of identification. This might include a password combined with a one-time code sent to a mobile phone or a security token. Implementing MFA significantly mitigates the risk of compromised passwords allowing access to sensitive information.
Role-based access control (RBAC) is a crucial element in securing access by defining specific permissions for each user role. This granular control ensures that users only have access to the resources and data necessary for performing their assigned tasks, reducing the potential damage from a compromised account. With this structured access, only permitted actions are executable, preventing accidental or malicious data alteration, further bolstering the overall secure hosting environment.
Incorporating these access management procedures alongside the firewall significantly enhances the security posture of the entire system. This combination effectively prevents various unauthorized access attempts, safeguards sensitive data, and adheres to industry best practices, a critical element of secure hosting.
Implementing robust secure access management and user authentication alongside a strong firewall effectively strengthens the defenses against malicious actors, demonstrating a commitment to safeguarding data and maintaining the confidentiality and integrity of the hosted resources, a fundamental aspect of any modern secure hosting environment. Without this, the firewall alone can’t ensure the complete protection of the hosting environment.
Effective secure access management and user authentication are integral elements of a comprehensive security strategy. They complement the firewall’s role in creating a multi-layered security approach that protects against a broader range of threats.
Security Auditing and Compliance
Regular security audits are crucial for maintaining a secure hosting environment with a firewall.
These audits assess the effectiveness of the firewall in blocking unauthorized access and identify vulnerabilities that could be exploited by malicious actors.
A comprehensive security audit examines the firewall’s configuration, rule sets, and logging mechanisms to ensure they are up-to-date and aligned with industry best practices and regulatory requirements.
This process involves scrutinizing the firewall’s performance, looking for potential weaknesses or areas where improvements could be made to enhance security measures.
The findings from security audits inform crucial updates to the firewall’s configuration, bolstering the overall security posture of the hosting environment and safeguarding sensitive data from breaches.
These audits are often performed by external security specialists or internal teams with specialized skills. They are essential for maintaining compliance with relevant security standards and regulations, such as PCI DSS or HIPAA.
Implementing a robust security auditing program demonstrates a proactive approach to security, which is a key factor in building trust with clients and partners.
This critical step in maintaining a secure hosting environment with a firewall ensures the continuous protection of the data being hosted.
Moreover, regular security audits, combined with a properly configured firewall, are fundamental in preventing unauthorized access, data breaches, and other security incidents. This includes rigorous testing of the firewall itself to verify its continued effectiveness.
Consequently, a well-structured and regular security auditing process contributes significantly to a strong and secure hosting infrastructure.
In conclusion, robust secure hosting with a firewall is no longer a luxury but a necessity in today’s interconnected digital landscape.
The inherent vulnerabilities of online platforms, coupled with the escalating threat of cyberattacks, demand a proactive approach to data protection and system integrity.
This article has highlighted the crucial role of secure hosting with firewall in safeguarding sensitive data, preventing unauthorized access, and maintaining business continuity.
From protecting confidential client information to maintaining compliance with industry regulations, the benefits of a secure hosting environment with a robust firewall are undeniable.
By implementing a comprehensive firewall solution integrated into the secure hosting infrastructure, businesses can significantly reduce their risk profile, ensure the reliability of their online presence, and build a stronger foundation for future growth and innovation.
The essential need for secure hosting with firewall extends to all organizations, large or small, that rely on digital platforms for their operations. Failing to prioritize security can lead to significant financial losses, reputational damage, and legal repercussions.
Ultimately, secure hosting with firewall acts as a crucial first line of defense against an ever-evolving landscape of cyber threats. By establishing a secure infrastructure, businesses can confidently navigate the complexities of the digital world while ensuring the protection of their valuable assets and the trust of their stakeholders.
Therefore, the implementation of a reliable secure hosting solution with a properly configured firewall should be considered a top priority for any organization operating online.