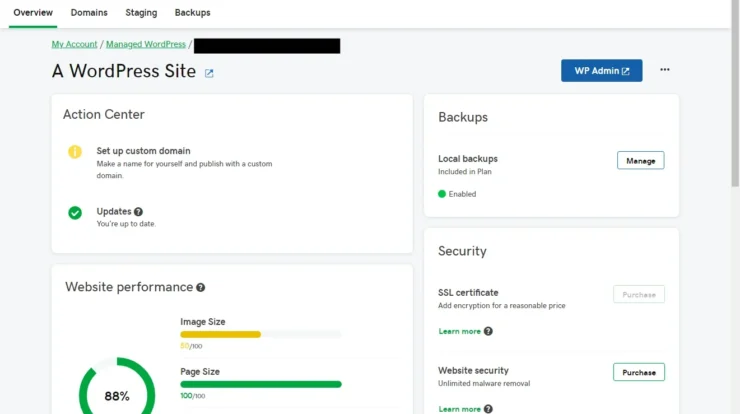
WordPress powers millions of websites worldwide, making it a prime target for malicious actors seeking to exploit vulnerabilities and compromise online presence.
Protecting these sites from malware is crucial for maintaining user trust, preventing data breaches, and upholding online reputation.
Ensuring secure WordPress hosting with robust malware protection is no longer a luxury, but a fundamental necessity for any website owner.
A compromised WordPress site can lead to significant financial losses, reputational damage, and legal repercussions, all of which can be avoided through careful selection of a hosting provider specializing in secure WordPress hosting.
This specialized hosting environment involves more than just standard server configurations; it entails proactive measures, including regular security audits, real-time malware scanning, and automated updates to WordPress core, plugins, and themes.
These meticulous security protocols can help safeguard sensitive data, ensuring uninterrupted site functionality, and ultimately improving the user experience.
Choosing the right secure WordPress hosting provider means selecting a service that understands the specific needs of WordPress installations, offering dedicated resources and expertise to handle evolving threats and maintaining high uptime.
Today’s sophisticated cyberattacks require equally sophisticated defenses. A robust secure WordPress hosting solution equipped with robust malware protection is the first line of defense against these sophisticated threats.
Understanding the intricacies of secure WordPress hosting, including the crucial element of malware protection, is essential to maintain the integrity of your online presence and safeguard your valuable data.
The Crucial Role of Proactive Malware Protection in Secure WordPress Hosting
A cornerstone of secure WordPress hosting is the proactive implementation of malware protection strategies.
This proactive approach is essential for safeguarding WordPress websites from the ever-present threat of malicious attacks, which are a significant concern for website owners.
A robust system for detecting and eliminating malware is an integral part of a comprehensive security strategy for WordPress hosting.
The benefits of robust malware protection extend beyond simply preventing infections; they also include the timely identification and removal of malicious code, thus minimizing the potential for significant damage.
Implementing real-time malware scanning is a crucial aspect of this protection. This technology continuously monitors files and applications for suspicious behavior.
Regular security audits play a vital role in identifying vulnerabilities and gaps in the security measures, allowing for timely corrective action.
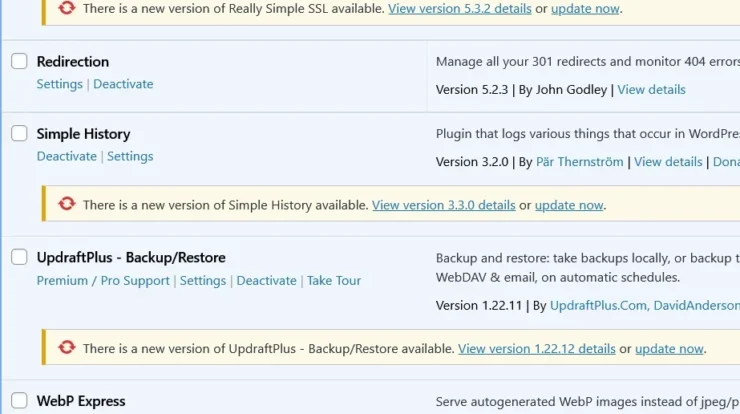
A proactive approach to malware protection also involves deploying regular updates to WordPress core files, themes, and plugins. This ensures that the software remains current and patched against known exploits.
The ability to detect threats at their source, before they have a chance to inflict damage, highlights the significance of secure WordPress hosting and its emphasis on proactive defense.
This proactive approach ensures the security of visitor data, preventing data breaches and maintaining the integrity of the website.
By employing these proactive measures, hosting providers can safeguard the website from various types of malware, including viruses, Trojans, and ransomware.
Employing such robust protection methodologies is a key differentiator for reliable secure WordPress hosting providers, setting them apart from those offering only basic hosting services.
A hosting provider specializing in secure WordPress hosting will often employ sophisticated security tools and protocols to prevent and address malware threats, contributing greatly to the site’s online safety.
This commitment to proactive malware protection ensures a secure environment for website owners, helping maintain visitor trust and promoting their reputation in the digital landscape.
Ultimately, a secure WordPress hosting environment with robust malware protection is a vital investment in website longevity and online presence.
The Crucial Role of Proactive Malware Protection in Secure WordPress Hosting
A cornerstone of secure WordPress hosting is the proactive implementation of malware protection strategies, essential for safeguarding websites from malicious attacks.
Proactive malware protection goes beyond simply reacting to intrusions; it demands a comprehensive approach that anticipates and mitigates potential threats.
This proactive stance is integral to preventing website compromise, ensuring data security, and maintaining user trust.
A robust system for detecting and eliminating malware is a critical component of a comprehensive security strategy for WordPress hosting.
This proactive security posture encompasses a range of technical measures, including regular security audits and continuous monitoring for suspicious activity.
Real-time malware scanning is a crucial aspect of proactive malware protection, constantly monitoring files and applications for any suspicious behavior.
Automated updates to WordPress core files, plugins, and themes are vital for patching vulnerabilities quickly, reducing the risk of exploitation by malicious actors.
A proactive approach also includes regularly updating server software, configurations, and security patches to stay ahead of evolving threats.
A comprehensive malware protection strategy involves identifying and responding swiftly to any identified vulnerabilities.
Advanced threat intelligence and signature-based detection systems enhance the effectiveness of malware protection measures, allowing for early identification of new and emerging threats.
The immediate identification and removal of malicious code minimize the scope and impact of potential damage.
Regular security audits, conducted by expert security professionals, help pinpoint vulnerabilities and weaknesses in the hosting infrastructure and website itself.
Furthermore, well-designed access controls and user authentication strengthen security protocols and limit unauthorized access to sensitive data.
Security measures should extend to the hosting environment itself, to prevent attackers from gaining unauthorized access to the server.
By integrating a secure WordPress hosting provider’s proactive malware protection strategies, website owners significantly lessen the likelihood of malware compromise.
Implementing these strategies prevents not only the initial infection but also the potential for data breaches, financial losses, and reputational damage.
This proactive approach distinguishes secure WordPress hosting from standard hosting, focusing on constant vigilance and prevention rather than just reactive measures.
Consequently, the best secure WordPress hosting services prioritize proactive security measures that anticipate and prevent potential malware issues, safeguarding the site from compromise.
A comprehensive strategy for proactive malware protection in secure WordPress hosting ensures website owners can focus on their core business objectives, knowing their online presence is shielded against the relentless threat of malicious attacks.
Robust Malware Scanning and Removal Processes
Robust malware scanning and removal processes are crucial for maintaining a secure WordPress hosting environment.
This involves implementing sophisticated automated and manual processes that effectively detect, analyze, and eliminate malware threats from WordPress websites hosted on a secure platform.
A comprehensive malware protection strategy should incorporate multiple layers of defense to safeguard against evolving threats.
A key aspect of this security approach is continuous scanning of files and databases, proactively identifying and quarantining suspicious code or modifications.
This proactive approach goes beyond simply reacting to known threats and includes regularly updating scanning engines to keep pace with emerging malware types and techniques.
Such a secure WordPress hosting solution needs to employ sophisticated algorithms for analyzing website code, identifying suspicious patterns, and detecting potentially malicious plugins and themes.
Additionally, real-time monitoring of server activity is essential to identify and respond to any unusual behavior or suspicious traffic that might indicate an intrusion attempt.
Regular security audits, including manual code reviews and penetration testing, enhance the effectiveness of automated security measures and identify potential vulnerabilities that automated systems may miss.
Automated systems, while valuable, should not replace expert human intervention, which is vital for deep dives into complex issues, investigating suspicious files and database entries, and discerning between false positives and genuine malware threats.
A strong malware protection strategy also entails automatic backups and restoration capabilities in case of compromise.
Secure WordPress hosting providers leverage a multi-layered approach to detect and remove malware, ensuring that the websites hosted on their platform are protected against malicious code and intrusions.
The use of advanced and comprehensive anti-malware tools is critical, employing a robust combination of signatures, heuristic analysis, and behavioral detection to scan for and identify even sophisticated and zero-day malware threats.
These automated systems should include continuous updates to ensure that the detection capabilities are consistently updated to combat new and emerging threats.
Furthermore, it is vital to have a streamlined and efficient process for removing malware once it’s detected.
This process should include steps for quarantining infected files or databases, restoring from backups, and patching vulnerabilities to prevent future infections.
A crucial element in a secure WordPress hosting environment is a fast and effective response to potential malware infections, including isolating affected websites to prevent further damage.
This robust process of scanning, removal, and preventative measures ensures the integrity and security of the WordPress hosting environment, safeguarding against the ever-present threat of malware.
A reliable secure WordPress hosting provider must have a system in place to address security issues promptly, preventing potential damage to user websites and data by effectively implementing malware protection strategies.
Comprehensive Malware Scanning and Remediation
A robust WordPress hosting solution must go beyond basic security measures and actively scan for and eliminate malware threats.
This proactive approach involves employing advanced scanning techniques to identify malicious code, including known vulnerabilities and suspicious file modifications that could indicate an infection.
Comprehensive malware scanning extends beyond simple file checks, incorporating code analysis, behavior monitoring, and regular security audits to detect even sophisticated, zero-day threats targeting WordPress websites.
The goal of these scans is to identify and quarantine malicious files and plugins, preventing them from causing further damage to the website and potentially affecting user data.
Beyond detection, a secure WordPress hosting platform must have a well-defined remediation process. This includes automated or manual removal of malicious code, ensuring that the website is completely free from any remnant threats and that sensitive data is not compromised. This secure WordPress hosting functionality often involves restoring from a clean backup, an essential step in the remediation process.
The remediation process also includes the blocking of any malicious IP addresses or domains attempting to further compromise the hosting environment, a critical component of maintaining a safe and secure WordPress hosting environment. Furthermore, a good secure WordPress hosting solution provides comprehensive security and support to help users mitigate the risk of future attacks, helping to maintain the integrity of their website.
These proactive measures for malware detection and remediation are critical to maintaining the integrity and functionality of a WordPress website, safeguarding it from harm and ensuring a smooth user experience. This is part of the essential package for any business or individual looking to host a WordPress site with confidence and peace of mind.
In today’s digital landscape, a robust and secure WordPress hosting environment is no longer a luxury, but a critical necessity for any website owner.
The vulnerability to malware attacks, coupled with the potential for data breaches and devastating reputational damage, underscores the importance of prioritizing secure WordPress hosting with comprehensive malware protection.
This article has highlighted the crucial steps involved in choosing and maintaining a secure WordPress hosting environment, emphasizing the need for reliable security measures to protect against the constant threat of cyberattacks.
From the outset, we’ve emphasized the importance of selecting a hosting provider that prioritizes security, offering features like real-time malware scanning, automatic backups, and robust firewall configurations. These robust security measures are essential for maintaining website integrity and user trust in an era where cyber threats are ever-evolving.
Ultimately, secure WordPress hosting with effective malware protection safeguards your website, data, and reputation. By investing in a reliable hosting provider that understands and implements these critical security measures, website owners can confidently navigate the online environment, knowing their digital assets are shielded from the risks associated with cyber threats. This ensures that your WordPress site remains a valuable and accessible online presence, rather than becoming a target for malicious actors. Prioritizing secure WordPress hosting with comprehensive malware protection is, therefore, a crucial element of long-term online success.